Table of Contents
ToggleIn an era where information security is paramount, the concept of “protected text” has become increasingly important. Whether it’s personal data, sensitive business information, or confidential communications, ensuring that your text remains secure and protected is crucial. This blog post will delve into the various aspects of protected text, its significance, methods of protection, and best practices for maintaining text security.
What is Protected Text?
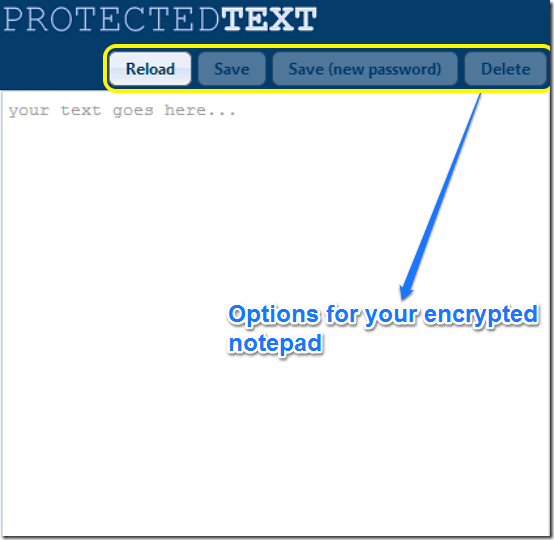
Protected text refers to any written information that has been secured through various means to prevent unauthorized access, alteration, or destruction. This protection can be achieved through encryption, password protection, access controls, and other security measures. The goal is to ensure that only authorized individuals can access and manipulate the text.
Why is Protected Text Important?
The importance of protected text cannot be overstated in today’s digital landscape. Here are several reasons why it is essential:
- Privacy: Personal information, such as social security numbers, addresses, and financial details, needs to be kept private. Protected text ensures that this information is not accessible to unauthorized individuals.
- Confidentiality: Businesses and organizations often deal with sensitive data, including trade secrets, client information, and strategic plans. Protected text helps maintain the confidentiality of this information.
- Data Integrity: Protecting text ensures that the information remains unaltered and accurate. Unauthorized changes to critical documents can lead to significant issues, including financial loss and reputational damage.
- Compliance: Many industries are subject to regulations that require the protection of certain types of information. Compliance with these regulations often necessitates the use of protected text.
Methods of Protecting Text
There are several methods available to protect text, each offering different levels of security and suitability depending on the context.
Encryption
Encryption is one of the most effective ways to protect text. It involves converting readable text into an unreadable format using algorithms and encryption keys. Only those with the correct decryption key can revert the text to its original form.
- Symmetric Encryption: Uses the same key for encryption and decryption. It is fast and efficient but requires secure key management.
- Asymmetric Encryption: Uses a pair of keys (public and private) for encryption and decryption. It provides enhanced security but is slower and more complex.
Password Protection
Password protection is a simple yet effective way to secure text. By setting a password, you can restrict access to the document or file containing the text.
- Strong Passwords: Use a combination of letters, numbers, and special characters to create a strong password that is difficult to guess.
- Password Management: Use password management tools to store and manage passwords securely.
Access Controls
Access controls involve setting permissions to determine who can access, modify, or share the protected text. This method is commonly used in collaborative environments and document management systems.
- Role-Based Access Control (RBAC): Assigns permissions based on the user’s role within an organization.
- Discretionary Access Control (DAC): Allows document owners to decide who can access their documents.
- Mandatory Access Control (MAC): Enforces strict policies that determine access based on predefined rules.
Digital Signatures
Digital signatures provide a way to verify the authenticity and integrity of a document. By applying a digital signature, you can ensure that the text has not been tampered with and that it comes from a verified source.
- Public Key Infrastructure (PKI): Uses a hierarchical system of digital certificates and keys to create and verify digital signatures.
Best Practices for Maintaining Protected Text
To ensure that your protected text remains secure, it is essential to follow best practices. Here are some recommendations:
- Regular Updates: Keep your encryption algorithms, software, and access control systems up to date to protect against new vulnerabilities.
- Employee Training: Educate employees on the importance of information security and best practices for handling protected text.
- Backup and Recovery: Implement a robust backup and recovery plan to ensure that protected text can be restored in case of data loss.
- Audits and Monitoring: Conduct regular security audits and monitor access to protected text to detect and respond to potential security breaches.
- Use of Secure Tools: Utilize tools and platforms that offer built-in security features for protecting text, such as encrypted messaging apps and secure document management systems.
Common Use Cases for Protected Text
Protected text is used in various scenarios to ensure the security and integrity of information. Some common use cases include:
- Business Communications: Protecting emails, contracts, and internal documents to maintain confidentiality and prevent data breaches.
- Legal Documents: Ensuring that legal documents, such as contracts and agreements, are secure and have not been altered.
- Medical Records: Protecting patient information and medical records to comply with privacy regulations like HIPAA.
- Financial Data: Securing financial statements, tax documents, and other sensitive financial information from unauthorized access.
Conclusion
In conclusion, protected text is a critical component of information security in the digital age. By understanding the importance of protecting text and implementing appropriate methods, individuals and organizations can safeguard their sensitive information from unauthorized access and tampering. Whether through encryption, password protection, access controls, or digital signatures, there are various ways to ensure that your text remains secure. Adhering to best practices and staying vigilant about information security will help maintain the integrity and confidentiality of protected text.
By incorporating these strategies and understanding the significance of protected text, you can better protect your data and ensure that it remains secure and confidential.